Following major law enforcement takedowns, the ransomware world is splintering, with scattered affiliates reorganizing and criminals rebranding under fresh banners.
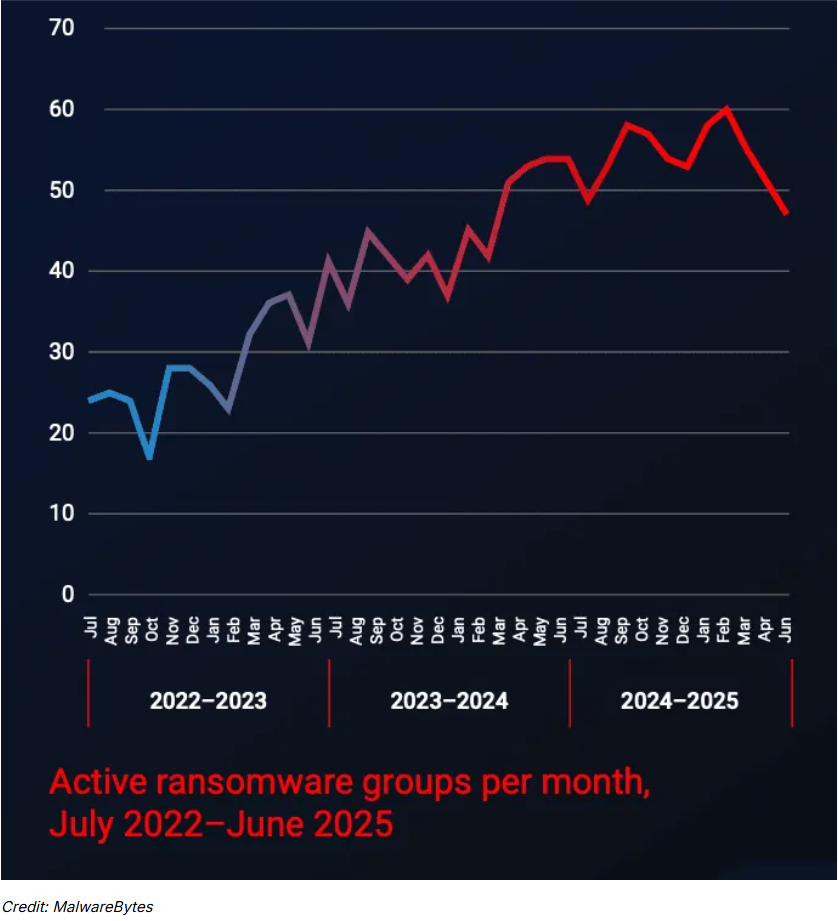
Observers are sounding the alarm over the surge of ransomware operations, as MalwareBytes recorded 41 new groups emerging from July 2024 to June 2025, bringing the overall count to more than 60 — a record high since data collection started.
“Whether this reflects more participants or smaller group sizes, it suggests that something — perhaps a mix of domain experience, commoditized malware, and abundant AI — is lowering the barrier to entry,” the company said last week.
“This steady growth in active ransomware groups has been fueled by consistent patterns of formation, closure, and activity. Over the last three years, approximately 50 new groups have appeared each year, around 30 have exited, and a typical group has attacked around five targets per month.”
Authorities in the U.S. and Europe have scored wins against large ransomware groups like LockBit, BlackCat/AlphV, and Hive, crippling their infrastructure. Yet the lack of significant arrests has left threat actors able to rebrand and form fresh operations.
In a report released last week, cybersecurity company Flashpoint analyzed ransomware-as-a-service (RaaS) actors, noting that numerous new groups are rebrands of shuttered operations. Flashpoint also observed that some gangs are leveraging leaked ransomware code to fuel attacks.
“For example, top ransomware group SafePay shares code with LockBit. The fingerprints of other notable ransomware groups, like Conti, are also apparent in the codebase of other ransomware groups,” they said.
According to Recorded Future’s ransomware specialist Allan Liska, the risks of operating a large RaaS outfit have grown “incredibly dangerous,” thanks to the effectiveness of the international Ransomware Task Force created during Joe Biden’s presidency. The remarks appeared in The Record, which operates independently as part of Recorded Future.
According to Liska, ransomware operations that make it too easy to onboard affiliates expose themselves to danger, as this opens the door for potential infiltration by law enforcement.
“So, ransomware affiliates are left with two choices: try to join one of the still operating closed groups like Qilin or Akira or start up their own ransomware operation,” Liska said.
According to MalwareBytes, the top 10 ransomware groups are losing dominance, accounting for just 50% of attacks today compared to 69% in 2022 — a sign of increasing fragmentation across the ecosystem.
Malwarebytes noted that the ransomware ecosystem remains highly volatile, as even the top 15 groups in a given year have sometimes faded almost entirely by the next.

