Threat actors are leveraging SendGrid’s credibility in a refined phishing campaign that bypasses traditional email security filters.
Cybercriminals use SendGrid’s cloud-based platform to send deceptive emails that appear legitimate to unsuspecting recipients.
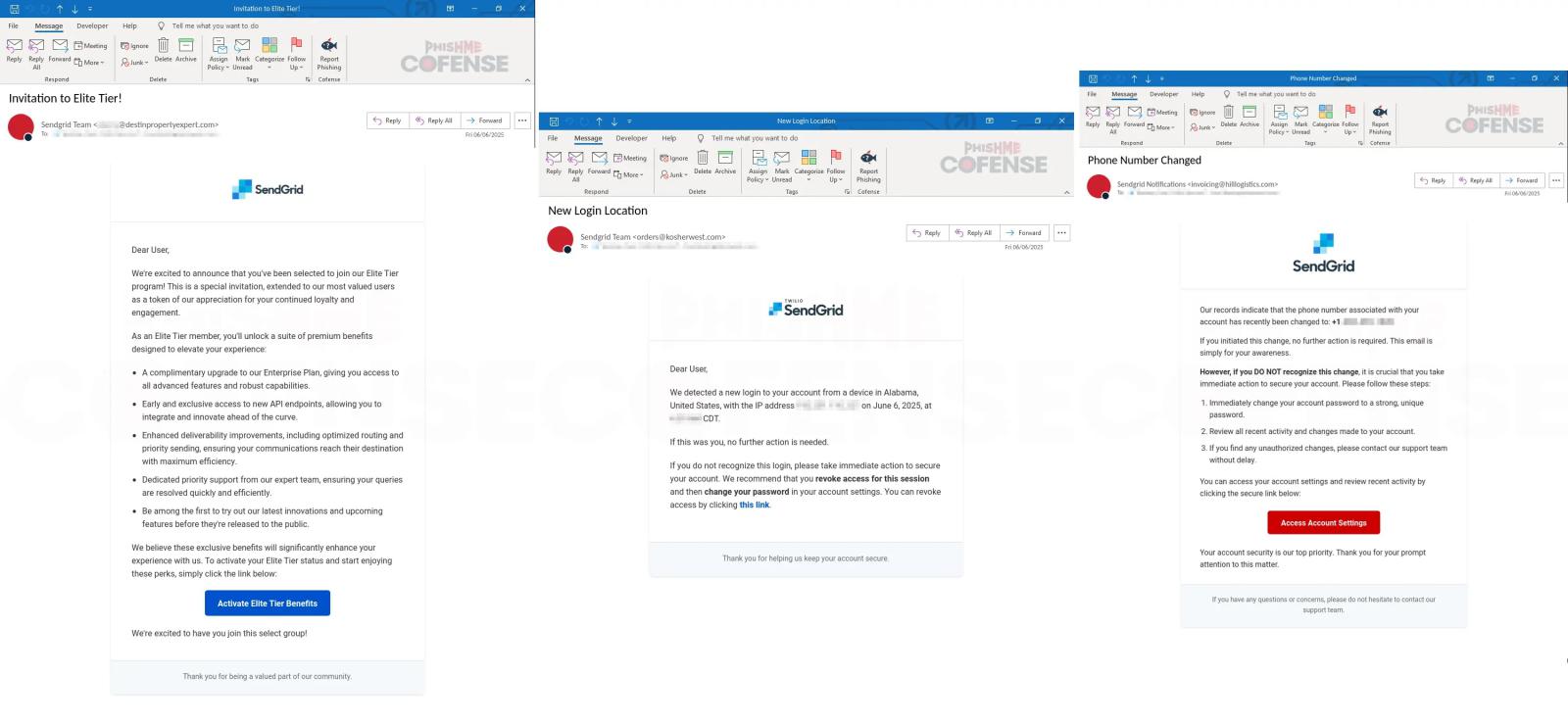
The attack uses multiple tactics, deploying three different email themes crafted to trigger urgency and exploit human behavior.
Every email copy mimics SendGrid’s style while relying on falsified sender information to strengthen believability.
The campaign leverages the reputation of a known provider, complicating detection for conventional security systems.
Attackers crafted the emails with professional layouts, precise branding, and formatting that mirrors authentic SendGrid communication.
The campaign thrives on psychological tricks, from fake login alerts with bogus IPs to tempting premium upgrade offers.
Researchers at Cofense, working through their Phishing Defense Center, flagged the campaign’s advanced psychological tactics.
The campaign leverages open redirect vulnerabilities, using domains such as url6849[.]destinpropertyexpert[.]com/ls/click? to craft credible redirect paths.
The technique disguises malicious intent by using reputable domains, ultimately redirecting users to phishing hosts such as loginportalsg[.]com.
Dissecting the Redirect Chain Exploitation
Attackers rely heavily on open redirect vulnerabilities in genuine domains, building sophisticated URLs that accept arbitrary inputs to enable hidden redirection to phishing endpoints.
The redirect mechanism follows this pattern:-
hXXp://url6849[.]destinpropertyexpert[.]com/ls/click?upn=[encoded_parameters]
Attackers use base64-encoded payloads in the URLs, leading users to counterfeit SendGrid login portals.
The encoded parameters are used to conceal the true destination, bypass URL reputation checks, and track victims for attackers.
The parameters are encoded to mask final targets, slip past security checks, and track users for attackers.
When decoded, the parameters lead victims to phishing pages on IP 185.208.156.46, hosting both loginportalsg[.]com and sendgrid[.]aws-us5[.]com.
Attackers crafted the landing pages to look nearly identical to SendGrid’s official interface. By copying branding elements, they increase the likelihood that victims will trust the fake login portal and enter credentials.
(Images Courtesy: Source – Cofense)

